University IT provides guidelines and training for safeguarding data and other sensitive information from cybercriminals.
Building on October as cybersecurity awareness month, University IT is highlighting its “Protect the House” campaign, which provides the “dos and don’ts” of safeguarding sensitive information at the University of Rochester every day of the year. Protect the House speaks to the responsibilities University community members have to safeguard our at-work information, as well as our personal information, in order to prevent cybercriminals from accessing data contained within the University and UR Medicine affiliates.
“Protecting the University house” requires both:
- investments in modern hardware and software to fence off the perimeters, secure University systems and networks, and
- a security culture, where each of us recognizes threats like phishing and breaches so we can make smart decisions like using strong passwords and multi-factor authentication.
Investing in new digital applications and services in University research, patient care, and academic pursuits without also safeguarding information systems and networks exposes the University to increasing levels of threats from cybercriminals who use increasingly sophisticated tools and methods to take advantage of human mistakes and fears. Breaches are also costly, both in terms of operational disruptions and financial costs.
“These transformations are not easy and University leadership is acutely aware that we must balance good security control with the need for efficient access to information,” says Julie Myers, vice president of information technology and chief information officer. “Ultimately, the aim of our Protect the House program is to ensure that the right people have the right level of access to the right data and systems at the right time. However, technical solutions cannot do all the work. For us to be successful, we all must embrace changes and take seriously our responsibility to recognize and avoid threats and prevent breaches.”
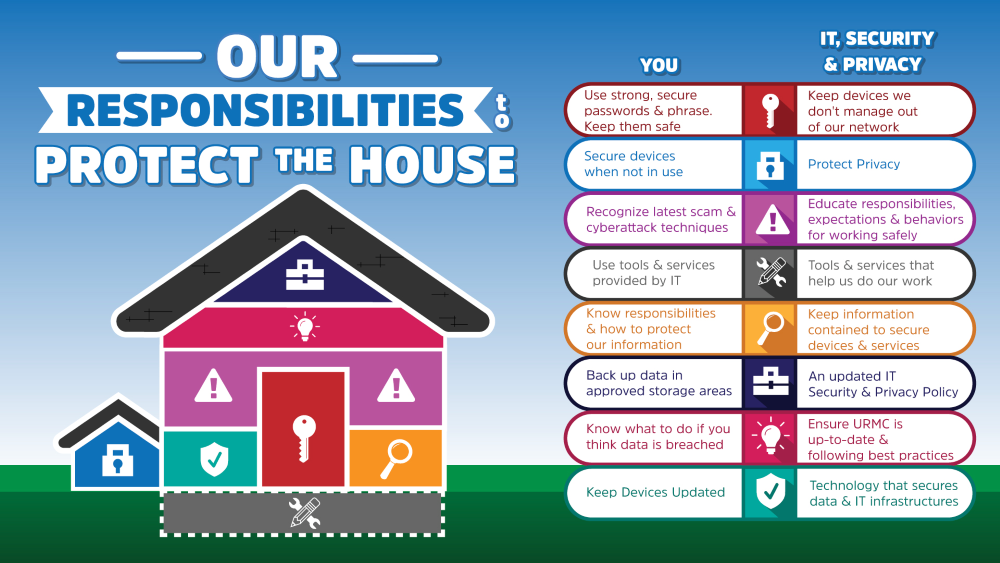
When it comes to ensuring a secure information culture, the following employee responsibilities help build a protective digital barrier around important data:
- Use strong, secure passwords and phrases. Keep them safe.
- Secure devices when not in use—shut them down or log off, and store in a safe place.
- Recognize the latest scams and cyberattack techniques.
- Use tools and services provided by University IT.
- Know your responsibilities and how to protect our information.
- Back up data in approved storage areas.
- Know what to do if you think data is breached.
- Keep devices updated.
As a reminder, all University faculty and staff are required complete by December 15 a training in MyPath called “Information Security Policy Updates.” It has been assigned to all staff, faculty, contractors, and student employees at the University and its affiliates, and is part of University IT’s bolstered institution-wide information security policies. The training helps to ensure everyone has a clear understanding of expectations, best practices, and responsibilities to keep personal and institutional information secure. It also helps individuals understand different levels of vulnerability and how to mitigate these threats:
- High risk: Social Security numbers, financial and bank information, personal health records, and other legally restricted and/or confidential information
- Moderate risk: budgets, organization charts with names, administrative data, research not marked confidential
- Low risk: public information available to all members of the University
Training take approximately 20 to 30 minutes and hourly employees can do the training during work hours; please work with your supervisors and managers to schedule your online course. Email University Information Security Risk and Compliance if you have questions.





